
- DDoS is a malicious attack in which an attacker disrupts a particular service thus making it unavailable to the genuine users.
- This can create huge market loss to companies as their services are disrupted.
- Most of the large MNC’s may not be vulnerable to this as their servers are capable of handling such huge requests.

How does DDoS happen?
- DDoS happens when various internet-connected devices infected with a particular malware allows the attacker to remotely instruct these malware infected devices (called zombies) to do what the attacker wants to. All the zombie devices together are called a botnet.
- What an attacker does is that, he may remotely instruct all the botnets to visit a specific site (that is target website) all at the same time.
- This imposes a heavy load on the server of that particular website which may ‘sometimes’ crash the server, thus disrupting the crucial services to genuine users.
- This may cause the entire website to go down until the ICMP packets (packets sent by attacker in order to crash the server) are manually flushed out of the server.
How to identify a DDoS attack?

- By checking the logs to see if a huge amount of traffic suddenly emerged from a single IP.
- The website suddenly gets slow or fails to load.
- Check if the website loads from any other device and if it fails, that site likely underwent a DDoS attack.
- As I’m not having access to multiple systems, I’ll perform a DoS attack on my local host in my Kali Linux.
- In linux we are going to use a tool called hping3 which is a tool very familiar reconnaissance tool Nmap.
- Hping3 is an open-source packet generator and analyser for TCP/IP protocol.
- Here, we are going to use a function in hping3 called ‘flood’.
- Flood is a function which floods the server with ICMP packets in order to overload the server and eventually crash it, leading to a DoS attack.
- Use the command listed below to start DoS attack using flood function.
Sudo hping3 -S –flood -V -p 80 <IP_to_attack>
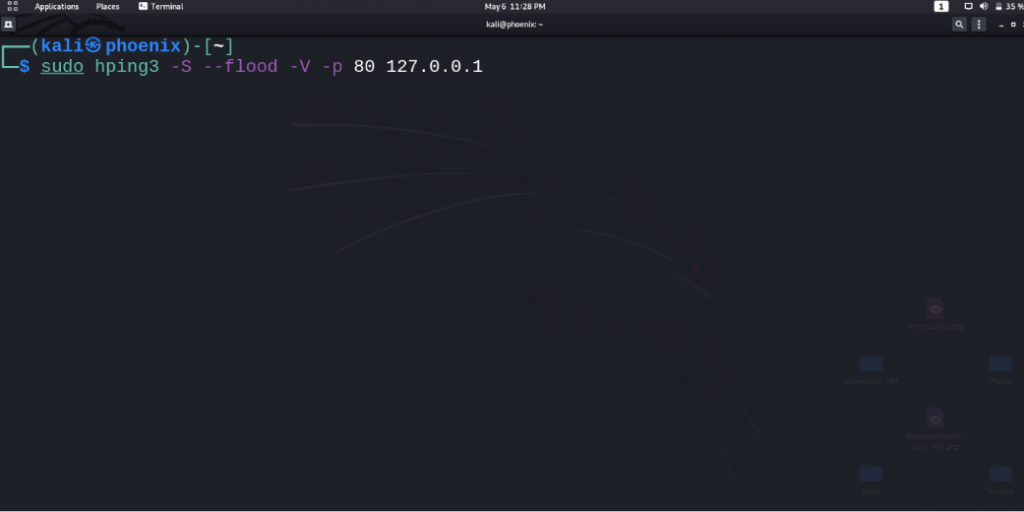
Abbreviations used:
- -S = SYN packets
- -V = Verbose results
- -p = port to attack
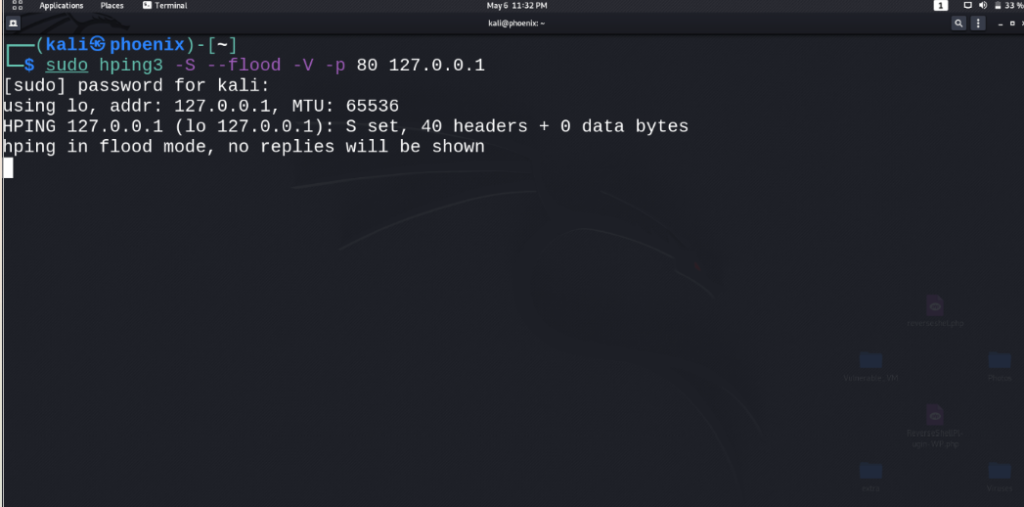
The above picture shows that flooding is taking place on the specified IP.
Note:
– You may not be able to crash a server with just a few devices as the server may be capable of handling such requests.
-Here, in my case I was just able to slow down my apache server (localhost) showing that a single device is not enough to even crash a local host server.
– As you would have already assumed, the servers of all major MNC’s like Google and YouTube are configured in such a way that the server ignores such unwanted flood requests from flooding their network.
Disclaimer
- This is for educational purposes only.
- Do not perform DoS attack’s on any target unless you have their explicit permission.
Live DDoS attack (Windows)
- Use a tool called HOIC (High-orbit-ion-cannon)
- HOIC is an open-source tool designed particularly for the purpose of performing DoS attacks.
- Download and install HOIC from Souceforge.net/hoic or click here
- HOIC is capable of attacking 256 URL’s at the same time.
- Add the required number of threads and add target IP.
- Click on button “FIRE THE LASER”
- It starts the DoS attack and as a result the website may slow down or even crash.
Summary
- The above-mentioned process depicts a DoS attack on the target.
- DDoS works in the same way. Just that the same process is executed remotely from multiple botnets at the same time.
- This imposes a lot of pressure on the server which may cause the server to crash and eventually leads to an DDoS attack.
You must be logged in to post a comment.